The Exploit Prevention component allows you to block malicious programs that use vulnerabilities of well-known applications. To determine whether an object is malicious, the component uses also the data from Dr.Web cloud service.
To enable or disable Exploit Prevention
1.Open Dr.Web menu ![]() , then select Security Center.
, then select Security Center.
2.In the open window, click Preventive Protection tile.
3.Enable or disable the Exploit Prevention component by using the switcher ![]() .
.
|
Depending on settings of your provider, the switcher |
Figure 68. Enabling/Disabling Exploit Prevention
To open Exploit Prevention parameters
1.Make sure Dr.Web operates in administrator mode (the lock at the bottom of the program window is open ![]() ). Otherwise, click the lock
). Otherwise, click the lock ![]() .
.
2.Click the Exploit Prevention tile. A component parameter window opens.
|
The component parameters can be adjusted if the provider enables this option.
Possibility to manage settings for different users can be disabled by your provider. In this case, all specified parameters are applied to all the users of the computer. |
In the window of component parameters, from the corresponding drop-down list, select the required level of protection against exploits.
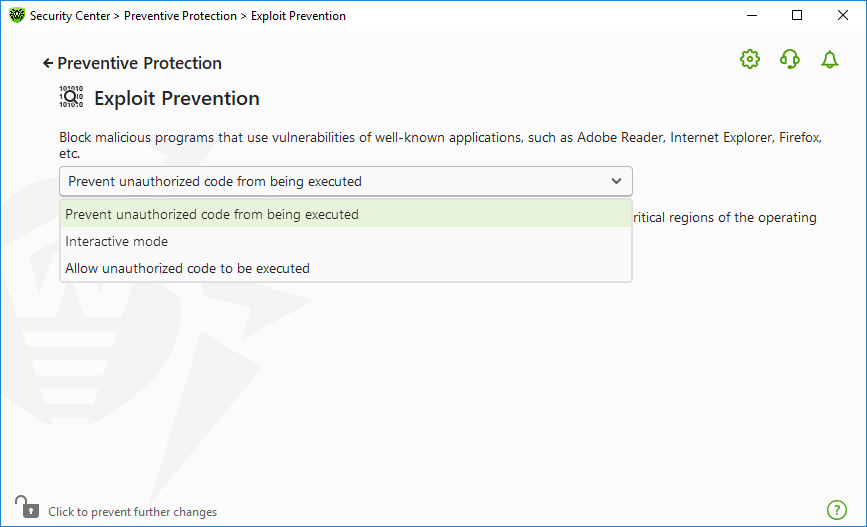
Figure 69. Selecting protection level
Protection levels
Protection level |
Description |
|---|---|
Prevent unauthorized code from being executed |
If an attempt of a malicious object to exploit software vulnerabilities in order to get access to critical regions of the operating system is detected, it will be blocked automatically. |
Interactive mode |
If an attempt of a malicious object to exploit software vulnerabilities in order to get access to critical regions of the operating system is detected, Dr.Web will display an appropriate message. Read the information and select a suitable action. |
Allow unauthorized code to be executed |
If an attempt of a malicious object to exploit software vulnerabilities in order to get access to critical regions of the operating system is detected, it will be allowed automatically. |
Receiving notifications
If necessary, you can configure desktop and email notifications on Exploit Prevention actions.
See also: