Check Results
|
How to open check results •If Dr.Web Scanner detects threats, the To open check results, tap the icon. •If SpIDer Guard detects a suspicious change in the system area or a threat, the following items appear on the screen: ▫An icon on the Android status bar in the top-left screen corner: ▪ ▪ ▫A pop-up notification about detection of a threat (see Figure 13). ▫The ▫A message with a red indicator on the status bar. To open check results, tap the
Neutralizing threats automatically When threats are detected, Scanner and SpIDer Guard neutralize them automatically. In the components settings you can choose, which actions will be applied to the threats.
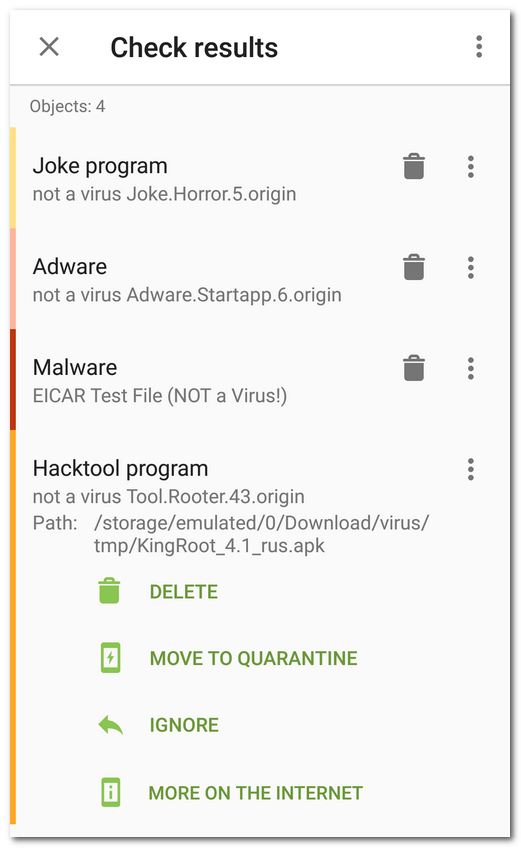
Depending on the threat type, the following options might be available: •Report. Notifies on threat detection. Then, you choose actions for each of them manually. •Move to quarantine. Sends threats to the isolated folder (see the Quarantine section). If the threat is detected in an installed application, it cannot be moved to quarantine and you need to neutralize it manually. •Cure, move to quarantine if incurable. Attempts to revert the infected files and applications to the safe state. If it fails, sends them to an isolated folder. Curing is available for some threats in system applications if root access is enabled on the device. If the threat is detected in an installed application, it cannot be moved to quarantine and you need to neutralize it manually. •Delete. Completely erases threats from the device memory. In some cases, Dr.Web cannot delete applications that use Android accessibility features. To remove such application manually, reboot to safe mode. The option is not available for threats in system applications in the following cases: ▫If root access is not allowed on your device. ▫If the application cannot be safely deleted. ▫If a threat modification is detected. To identify if the app does pose a threat, report a false positive. •Cure, delete if incurable. Attempts to revert the infected files and applications to the safe state. If it fails, completely erases them from the device memory. In some cases, Dr.Web cannot delete applications that use Android accessibility features. To remove such application manually, reboot to safe mode. Curing is available for some threats in system applications if root access is enabled on the device. •Ignore. Leaves threats as they are. Neutralizing threats manually Most of the threats are neutralized automatically according to the Scanner and SpIDer Guard settings. However, if Dr.Web uses centralized protection mode and connects to the server version 13.00.1 (17-03-2025 03:00:00) or earlier, you need to neutralize threats manually. Additionally, if Report is set up as the action for any threat type, you will also need to decide how to neutralize the detected threats of this type. To neutralize threats, tap On the neutralizing threats screen, you can review the list of threats and suspicious changes in the system area. For each object, its type and name are specified, as well as the icon of the recommended option for the object. Objects are marked in different colors depending on the degree of danger. Listed below are the threat types in decreasing danger order: 1.Malware. 2.Riskware. 3.Hacktool program. 4.Adware. •New files in system area. •Change of system files. •Deletion of system files. 6.Joke program. To view the file path, select the object. For threats that are detected in apps, the app package name is also specified. To delete all threats •In the top-right corner of the Check results screen, select Menu To move all threats to the quarantine •In the top-right corner of the Check results screen, select Menu Neutralizing one threat at a time Each object has its own set of available options. Recommended actions are placed first. To expand the list, select the object. Possible options include:
The option is available for some threats in system applications if root access is enabled on the device.
In some cases, Dr.Web cannot delete applications that use Android accessibility features. To remove such application manually, reboot to safe mode. The option is not available for threats in system applications in the following cases: •If root access is not allowed on your device. •If the application cannot be safely deleted. •If a threat modification is detected. To identify if the app does pose a threat, report a false positive.
If the threat is detected in an installed application, it cannot be moved to the quarantine. In this case, the Move to quarantine option is not available.
The option is available for threats in system applications.
If the file is sent to the laboratory successfully, the Ignore option is automatically applied to the object. The Send to laboratory option is available only for added or changed executable files in the system area: .jar, .odex, .so, APK, ELF files, etc. The False positive option is available only for threat modifications and for threats detected in the system area.
|