On this page, you can configure Dr.Web reaction to such actions of other programs that can compromise security of your computer and select protection level against exploits.
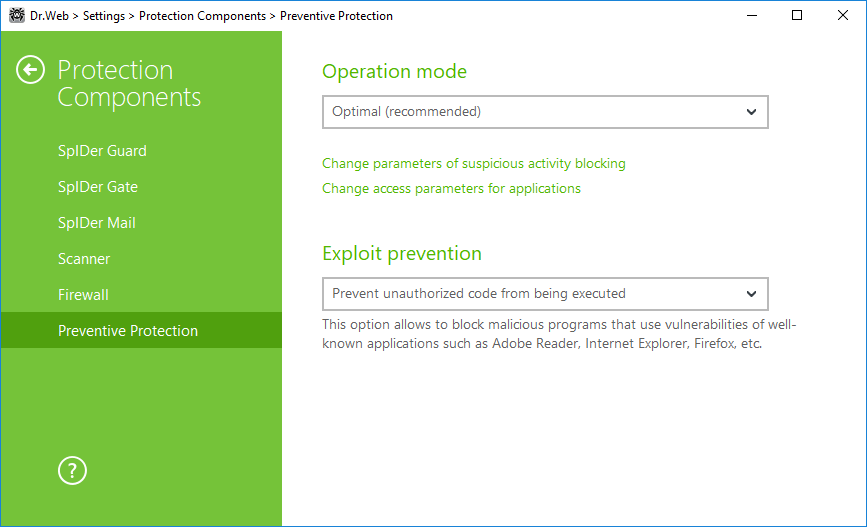
Figure 46. Preventive Protection settings
At that, you can configure a separate protection mode for particular applications or configure a general mode whose settings will be applied to all other processes.
To configure the general mode, select it from the Operation mode list or click Change parameters of suspicious activity blocking. As a result of the second action, a window opens providing you with details on each mode and editing options. All changes are saved in the User mode. In this window, you can also create a new profile for saving necessary settings.
To create a new profile
1.Click ![]() .
.
2.In the open window, enter a name for the new profile.
3.Look through default settings and, if necessary, edit them.
To configure preventive protection settings for particular applications, click Change access parameters for applications. In the open window, you can add a new rule or edit or delete an existing rule.
To add a rule
1.Click ![]() .
.
2.In the open window, click Browse and specify the path to the application executable file.
3.Look through default settings and, if necessary, edit them.
To edit an existing rule, select it from the list and click ![]() .
.
To delete an existing rule, select it from the list and click ![]() .
.
For more information about settings of each operation mode, refer to the Preventive Protection Level section.
Preventive protection level
In the mode Optimal mode , which is set by default Dr.Web disables automatic changes of system objects, whose modification explicitly signifies a malicious attempt to harm the operating system. It also blocks low-level access to disk and protects the HOSTS file from modification.
Only actions by the applications that are not trusted, are blocked. |
If there is a high risk of your computer getting infected, you can increase protection by selecting the Medium. In this mode, access to the critical objects, which can be potentially used by malicious software, is blocked.
Using this mode may lead to compatibility problems with legitimate software that uses the protected registry branches. |
When required to have total control of access to critical Windows objects, you can select the Paranoid. In this mode, Dr.Web also provides you with interactive control over loading of drivers and automatic running of programs.
With the User-defined mode, you can set a custom protection level for various objects.
Protected object |
Description |
|---|---|
Integrity of running applications |
This option allows detection of processes that inject their code into running applications. It indicates that the process may compromise computer security. Processes that are added to the Exclusions are not monitored. |
Integrity of user files |
This option allows detection of processes that modify user files with the known algorithm, which indicates that the process may compromise computer security. Processes that are added to the Exclusions are not monitored. To protect your data from modification, you can enable creation of protected copies that contain important data. |
HOSTS file |
The operating system uses the HOSTS file when connecting to the Internet. Changes to this file may indicate virus infection. |
Low level disk access |
Block applications from writing on disks by sectors while avoiding the file system. |
Drivers loading |
Block applications from loading new or unknown drivers. |
Critical Windows objects |
Other options allow protection of the following registry branches from modification (in the system profile as well as in all user profiles). Image File Execution Options: •Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options User Drivers: •Software\Microsoft\Windows NT\CurrentVersion\Drivers32 •Software\Microsoft\Windows NT\CurrentVersion\Userinstallable.drivers Winlogon registry keys: •Software\Microsoft\Windows NT\CurrentVersion\Winlogon, Userinit, Shell, UIHost, System, Taskman, GinaDLL Winlogon notifiers: •Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify Windows registry startup keys: •Software\Microsoft\Windows NT\CurrentVersion\Windows, AppInit_DLLs, LoadAppInit_DLLs, Load, Run, IconServiceLib Executable file associations: •Software\Classes\.exe, .pif, .com, .bat, .cmd, .scr, .lnk (keys) •Software\Classes\exefile, piffile, comfile, batfile, cmdfile, scrfile, lnkfile (keys) Software Restriction Policies (SRP): •Software\Policies\Microsoft\Windows\Safer Browser Helper Objects for Internet Explorer (BHO): •Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects Autorun of programs: •Software\Microsoft\Windows\CurrentVersion\Run •Software\Microsoft\Windows\CurrentVersion\RunOnce •Software\Microsoft\Windows\CurrentVersion\RunOnceEx •Software\Microsoft\Windows\CurrentVersion\RunOnce\Setup •Software\Microsoft\Windows\CurrentVersion\RunOnceEx\Setup •Software\Microsoft\Windows\CurrentVersion\RunServices •Software\Microsoft\Windows\CurrentVersion\RunServicesOnce Autorun of policies: •Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run Safe mode configuration: •SYSTEM\ControlSetXXX\Control\SafeBoot\Minimal •SYSTEM\ControlSetXXX\Control\SafeBoot\Network Session Manager parameters: •System\ControlSetXXX\Control\Session Manager\SubSystems, Windows System services: •System\CurrentControlXXX\Services |
If any problems occur during installation of important Microsoft updates or installation and operation of programs (including defragmentation programs), temporarily disable Preventive Protection.
If necessary, you can configure desktop and email notifications on Preventive Protection actions. |
Exploit prevention
This option allows to block malicious programs that use vulnerabilities of well-known applications. From the corresponding drop-down list, select the required level of protection.
Protection level |
Description |
Prevent unauthorized code from being executed |
If an attempt of a malicious object to exploit software vulnerabilities to get access to critical regions of the operating system is detected, it will be blocked automatically. |
Interactive mode |
If an attempt of a malicious object to exploit software vulnerabilities to get access to critical regions of the operating system is detected, Dr.Web will display an appropriate message. Read the information and select a suitable action. |
Allow unauthorized code to be executed |
If an attempt of a malicious object to exploit software vulnerabilities to get access to critical regions of the operating system is detected, it will be allowed automatically. |