Ransomware Protection allows detection of processes that attempt to encrypt user files using known algorithm that defines processes as a security threat. Ransomware is one of these processes. When entering a computer such malicious programs block access to user data and then demand ransom for decryption. They are considered among the most common malicious programs and cause great annual losses both to companies and ordinary users. The most common way of getting infected are bulk emails containing malicious files or a link to malware.
According to Doctor Web statistics, probability of restoring files compromised by encryption ransomware is only 10%, that is why the most efficient way of fighting it is to prevent the infection. Recently the number of users that have suffered such infection has decreased. However, the number of Dr.Web technical support requests for decryption reaches 1000 every month.
To enable or disable Ransomware Protection
1.Open Dr.Web menu ![]() , then select Security Center.
, then select Security Center.
2.In the open window, click Preventive Protection tile.
3.Enable or disable Ransomware Protection by using the switcher ![]() .
.
|
Depending on settings of your provider, the switcher |
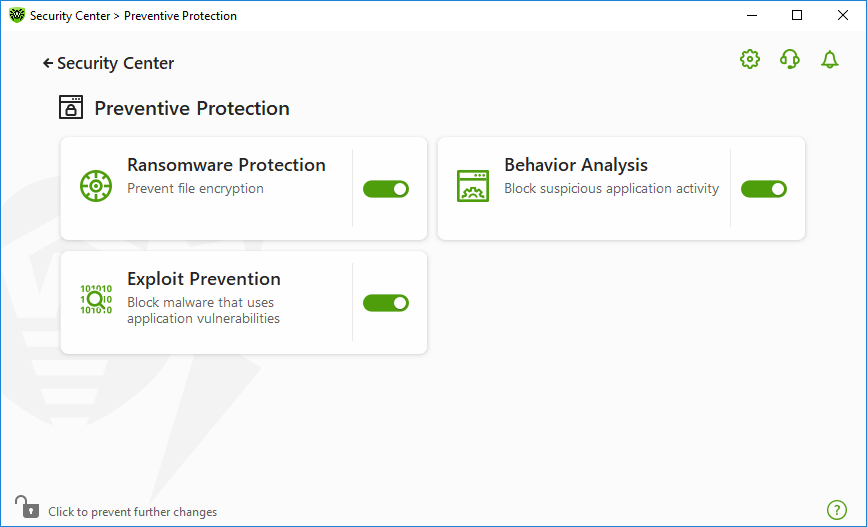
Figure 56. Enabling/Disabling Ransomware Protection
In this section:
•Configuring reaction to application attempts to encrypt files
Dr.Web reaction to application attempts to encrypt a file
To configure Ransomware Protection parameters
1.Make sure Dr.Web operates in administrator mode (the lock at the bottom of the program window is open ![]() ). Otherwise, click the lock
). Otherwise, click the lock ![]() .
.
2.Click the Ransomware Protection tile. A component parameter window opens.
3.In the drop-down menu, select an action to be applied to all applications.
|
The component parameters can be adjusted if the provider enables this option. |
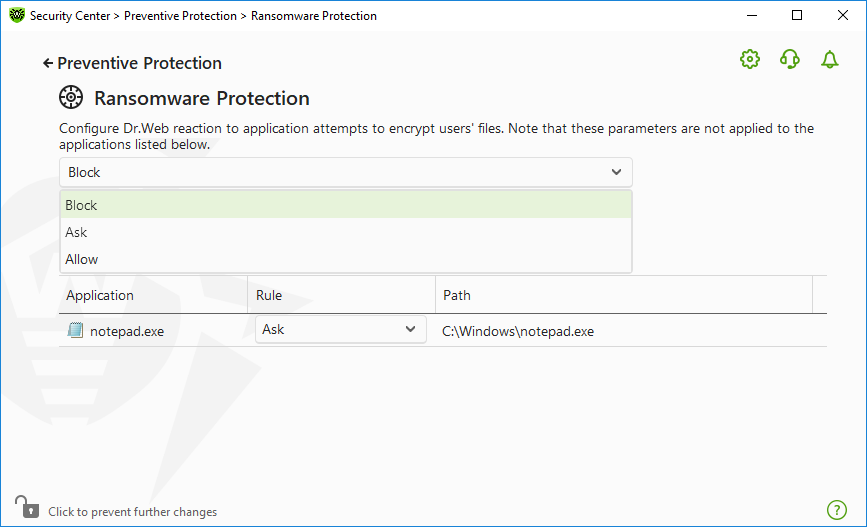
Figure 57. Selecting Dr.Web reaction
•Allow—all the applications are allowed to modify user files.
•Block—all the applications are not allowed to encrypt user files. This mode is enabled by default. When an application attempts to encrypt the user files following notification will be shown:
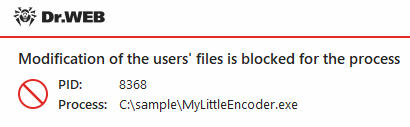
Figure 58. Notification example with a blocked application attempt to modify user files
•Ask—when an application attempts to encrypt a user file, a notification appears, where you can prevent the encryption or ignore it:
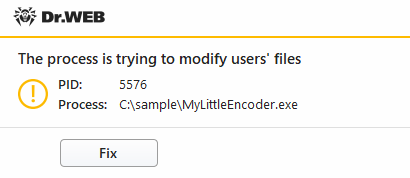
Figure 59. Notification example with an application attempt to modify user files
▫If you click Fix button the process is blocked and moved to quarantine. Even if the application is restored from the quarantine it cannot be launched until the computer restart.
▫If you close the notification window, the application will not be neutralized.
|
Depending on settings of your provider, the Allow mode can be also available. In such a mode, all the applications are allowed to modify user files. |
Receiving notifications
If necessary, you can configure desktop and email notifications on Ransomware Protection actions.
See also:
Separate rules for certain applications
You can configure Ransomware Protection reaction on actions of certain applications. For this, add applications to the list and select a necessary reaction of the component. The following management elements are available to work with objects in the list:
•The button—add the application to the list of applications with separate rules.
•The button—delete the application from the list of applications with separate rules.
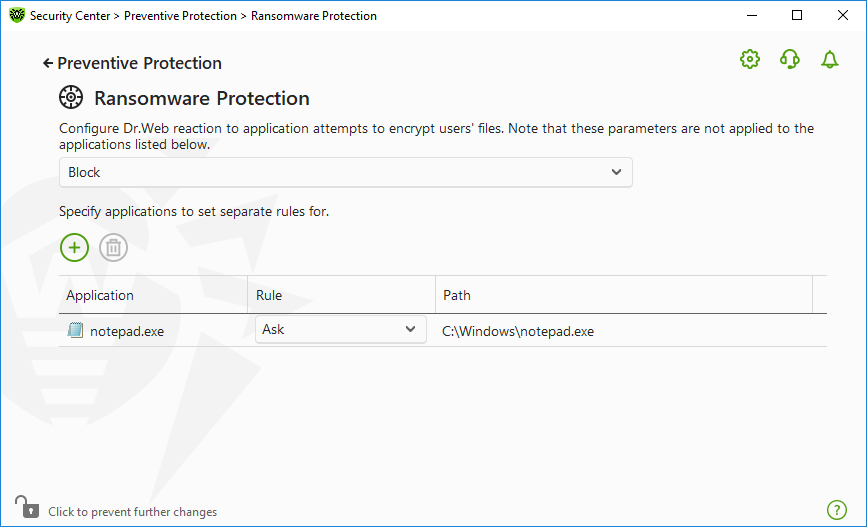
Figure 60. Excluding from Ransomware protection scanning
To add an application to the list
1.Click .
2.Do one of the following:
•In the open window, click the Browse button to select an application. You can also enter the full path to the application manually or use environment variables, for example:
▫C:\Program Files\folder\example.exe ▫%PROGRAMFILES%\folder\example.exe |
•Enter the application name in the field. The full path is not required, for example:
example.exe |
•To add applications, enter the defining mask of their names. ![]() More about masks;
More about masks;
A mask denotes the common part of object names, at that: ▫The asterisk (*) character replaces any, possibly empty, sequence of characters. ▫The question mark (?) replaces any character (one). Examples: ▫C:\Program Files\folder\*.exe—adds applications in the folder C:\Program Files\folder. Applications in subfolders will not be added. ▫C:\Program Files\*\*.exe—adds applications stored in the first nesting level subfolders of C:\Program Files. ▫C:\Program Files\**\*.exe—adds applications in subfolders of any nesting level located in the folder C:\Program Files. Applications in the folder C:\Program Files will not be added. ▫C:\Program Files\folder\exam*.exe—adds any application in the folder C:\Program Files\folder if their names begin with exam. In subfolders, these applications will be not be added. ▫example.txt—adds all applications with the name example and the .exe extension located in all folders. ▫example* —adds all types of applications with the name starting with example located in all folders. ▫example.*—adds all applications with the name example in all folders without regard for the extension. |
•You can add an application by the name of a variable if the name and a value of this variable are specified in the system variable settings ![]() example.
example.
%EXAMPLE_PATH%\example.exe – adds an application by the name of a system variable. A name of a system variable and its value can be specified, if needed, in the operating system settings. For Windows 7 and higher: Control Panel → System → Advanced system settings → Advanced → Environment variables → System variables. A name of a variable in an example: EXAMPLE_PATH. A value of a variable in an example: C:\Program Files\folder. |
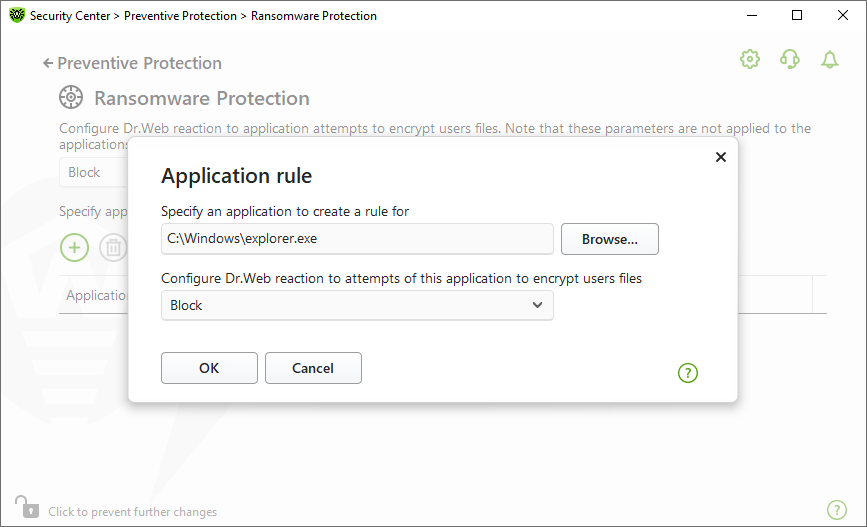
Figure 61. Selecting a rule for a certain application
3.Select a necessary component reaction from the drop-down list.
4.Click OK.
You can also change previously selected rule.
To change the Dr.Web reaction for applications with rules set
1.On the main window of the Ransomware Protection component, select the required application.
2.In the corresponding line in the Rule column select from the drop-down list the required reaction on application attempts to encrypt user files.
To protect your data from unauthorized changes, you can also add files to the list of protected files.