YARA is a malware detection and classification tool. It allows you to create rules using strings, boolean expressions, wildcards, regular expressions, special operators, and other.
This section provides tools for creating and working with YARA rules. For more information about the YARA rules, check YARA documentation.
In this section you can:
•search, filter and sort rules;
•monitor matches and navigate to the last match report;
•add, edit, delete, turn on/off the rules.
There are user and system rules. In the rules list, they’re marked as ![]() and
and ![]() accordingly. User rules are rules added within your account. System rules are added by the Dr.Web vxCube developers. You can disable any rule. Only user rules can be viewed, edited, or deleted.
accordingly. User rules are rules added within your account. System rules are added by the Dr.Web vxCube developers. You can disable any rule. Only user rules can be viewed, edited, or deleted.
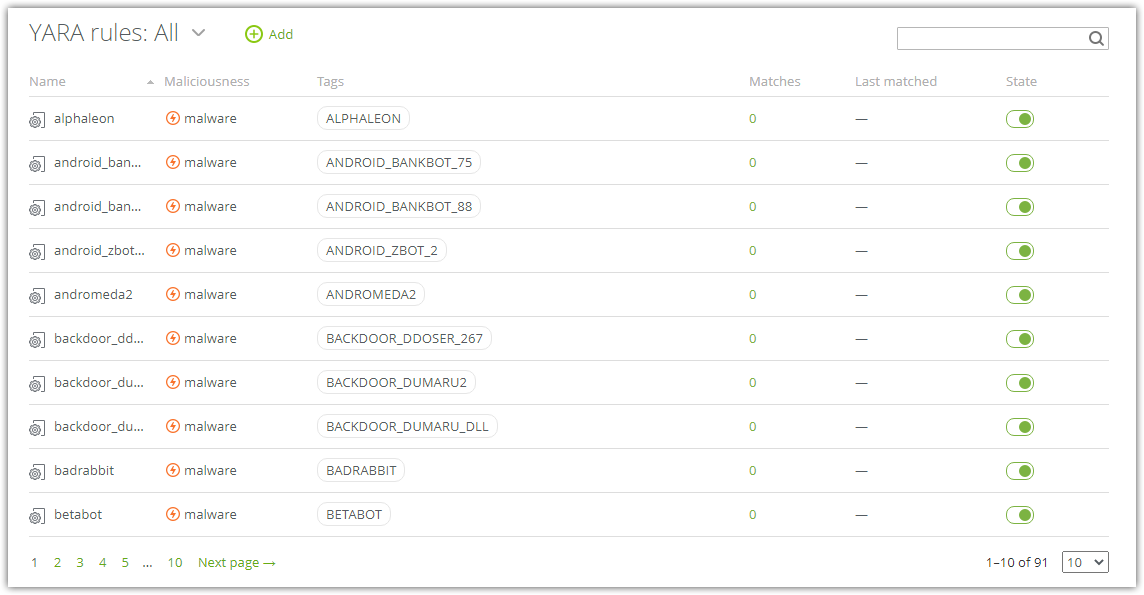
Figure 8. List of YARA rules
Creating the rules
Dr.Web vxCube provides advanced capabilities for working with YARA rules. In the meta section, you can specify a file behavior category to be displayed in the report if the rule matches. To create rules that are triggered on certain file behavior, you can use the dr_sandbox module.
To create a rule
1.Click ![]() Add. The window with sample rule code appears.
Add. The window with sample rule code appears.
2.In place of RuleName1 enter the rule’s name using letters, digits, or underscore.
3.Change TAG1 and TAG2 tags to your desired tags if necessary. They will be included in the report if this rule is triggered during the analysis.
4.Specify the file behavior category that will be assigned to the file if the rule is triggered. Possible values: "neutral", "suspicious", "malware”.
5.Add other parameters and conditions for the rule.
6.Click Add.
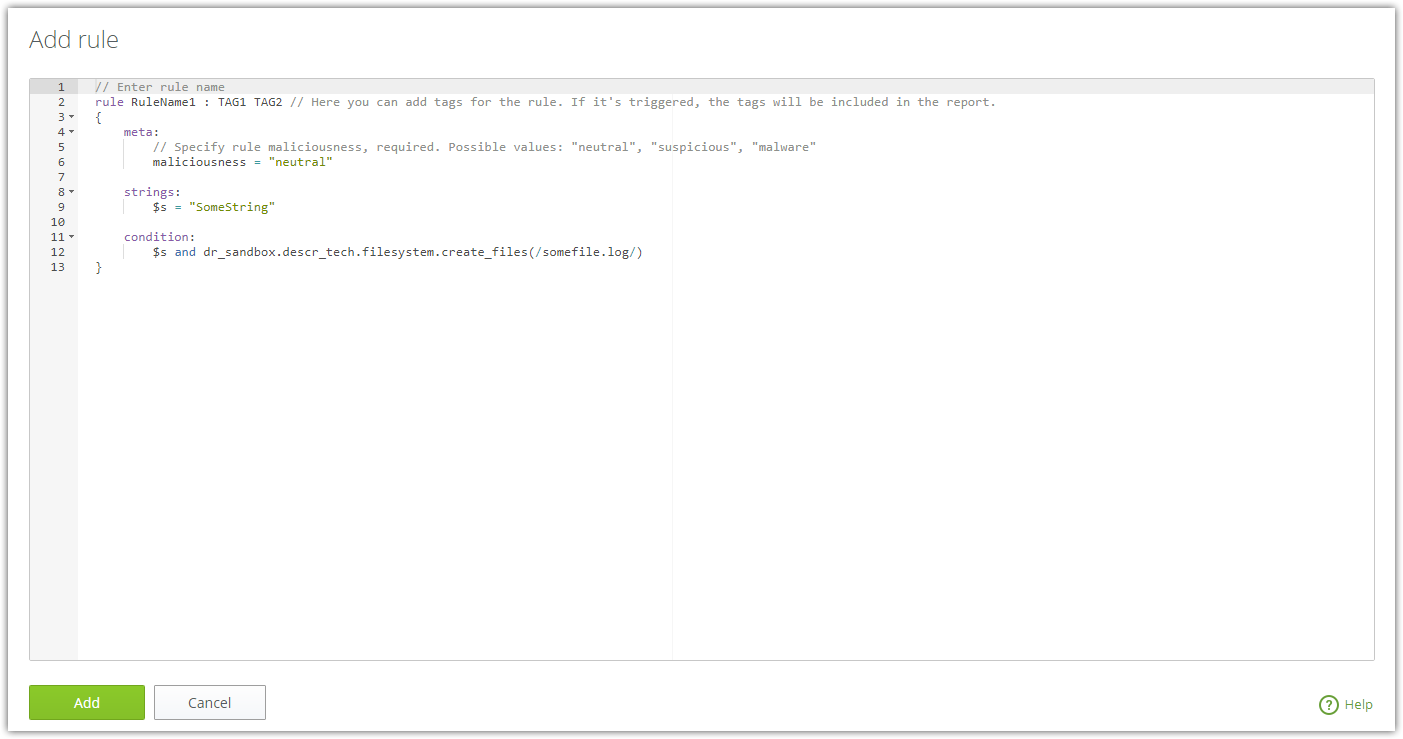
Figure 9. Add rule window
Managing the rules
To disable or enable a rule
•Point at the rule and click ![]() .
.
To edit a rule
•Point at the rule and click ![]() .
.
To delete a rule
•Point at the rule and click ![]() .
.
To set a number of rules displayed on one page
•Click the drop-down menu below the table.
To sort rules
•Click the corresponding column title.
To filter rules
•Enter your query in the search box. Search is done through names, tags and last matched columns.
•Next to the table name, you can choose to display system, user, or all rules.
Rules matches
To view reports on rules matches, click the number of matches in the row of the required rule.
A table will open displaying:
•information about the files on which the rule was triggered: file name, format, SHA1 hash;
•the date the rule was triggered;
•list of operating systems within which the analysis has been done.
To open a page with analysis report
•Click on the file name to go to the main page of the report.
•Click on the OS name to go to the platform report page.
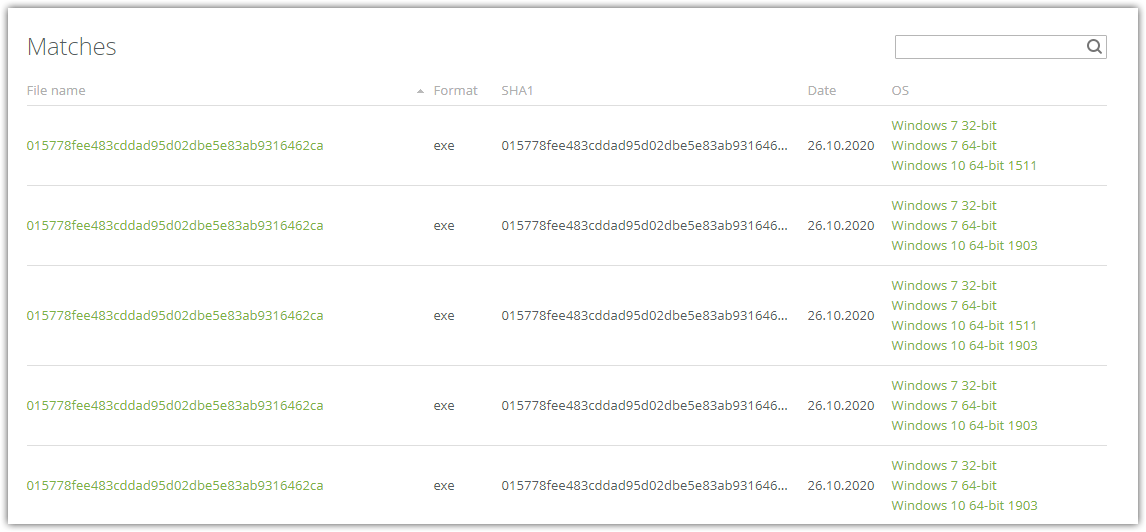
Figure 10. Report on YARA rule matches
The dr_sandbox module is an exclusive Dr.Web YARA module, which allows creating rules based on:
•information on the file behavior,
•types of created files (src, dump, drop, alloc and etc.),
•information about detected threats,
•the analyzed file’s name.
Sample rule that uses the dr_sandbox module:
rule bad_file |
A detailed list of the module's capabilities is in Appendix B. dr_sandbox module for YARA rules.