By default, Scanner uses all detection methods to detect viruses and other malicious software and during scanning:
•executable files processed with special compression utilities are unpacked and scanned;
•files within common archives are scanned (ACE, ALZIP, AR, ARJ, BGA, 7-ZIP, BZIP2, CAB, GZIP, DZ, HA, HKI, LHA, RAR, TAR, ZIP, etc.);
•files within file containers are scanned (1C, CHM, MSI, RTF, ISO, CPIO, DEB, RPM, etc.);
•messages stored within folders of mail programs are scanned (e-mail should be in the RFC822 format).
To start antivirus scan
1.On the context menu of the Agent, select Scanner. This opens the Scanner window.
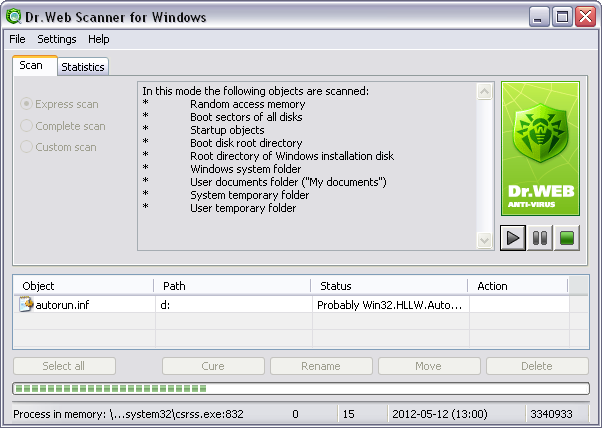
2.Before start the scan, select one of the following scanning modes at Scan Tab:
Further you could stop the running scan and set different scan mode.
3.If necessary, configure the scan settings in the Settings section.
Also, if necessary, change the default principle of actions set for detected malicious software (for details, see Actions Upon Detection), in the Actions settings section.
4.To manage scanning process, use the following buttons in the right part of the window:
•![]() Start - to start the scan;
Start - to start the scan;
•![]() Pause - to suspend scanning. To continue with the check, click
Pause - to suspend scanning. To continue with the check, click ![]() Start again;
Start again;
•![]() Stop - to terminate scanning.
Stop - to terminate scanning.
5.Scan results display in the bottom pane of the Scan tab and on the Statistics tab. The report table includes the following information:
Column |
Description |
|---|---|
Object |
Names of malicious or suspicious objects, boot sectors or memory processes. If malicious or suspicious objects are detected within compound objects such as archives, mail boxes or file containers, the report also lists complex objects containing them. |
Path |
Full path to malicious object (for files and boot sectors) or information on infected archive. |
Status |
For files and boot sectors: name of detected threat or its modification (a modification of a known virus is a code resulting from such alteration of a known virus that it can still be detected, but cannot be treated with the curing algorithms applied to the initial virus) according to the internal Doctor Web classification. For threats within complex objects, lists information on the complex object. For suspicious objects, indicates that the object is possibly infected and lists types of a possible threats according to the classification of the heuristic analyzer. |
Action |
Contains information on actions performed by the Scanner to deactivate malicious object. For example, curing, deletion, renaming, moving. If detected object is in use by another Windows application, no action can be performed immediately. For such objects, in the Scanner report section in the Action column, the Will be cured after reboot, Will be deleted after reboot or Will be renamed after restart string is displayed depending on the selected action. The action is performed after the next system reboot. If such objects are detected, it is recommended to reboot the system immediately after the scanning. |
To access different windows, menus and functions, you can also use ![]() hot keys
hot keys
F1 - help; F3 - main window, the Scan tab; F4 - main window, the Statistics tab; F5 - scan path and mask window; F7 - scan RAM and startup objects; F8 - start the automatic updating utility; F9 - Scanner settings tabs; F10 - switch to the main menu; CTRL+F5 - begin scanning; CTRL+F6 - stop scanning; CTRL+F2 - clear report list; ALT+X - exit. |
See also: